Vishing (voice phishing) is a type of social engineering attack which uses voice technology. Unlike other phishing attacks, such as email phishing and SMiShing that use emails and text messages respectively, vishing is a call-based attack. It tricks potential victims into revealing their sensitive and financial information such as account numbers, PIN, passwords, and more by impersonating a call from an authorized bank or a legitimate organization.
Under vishing, threat actors use fake caller ID in order to appear legitimate (such as your bank or your office) where they aim to encourage victims to divulge sensitive information, such as credit/debit card details, personal information, username & password, OTP (One Time Passwords), and bank account details or to install malicious software in your PC to monitor your online activities and steal data. As many services use automated callers (also known as robocall or bot caller) to lessen the burden on customer relations, this technology can also, for worse, be used as part of a voice phishing scam.

With continuous developments in technology, hackers have ramped up their game. The use of AI (artificial intelligence) has made some jaw-dropping advances in the attack surface. There have been reports of security incidents that involved the use of AI to impersonate trusted individuals to phish potential victims.
Vishing is also sometimes followed by other phishing attacks. For example, you click on a link for an ad that piques your curiosity. Unfortunately, you find that your system has been infected with ransomware or other malware that makes you believe that your system has been compromised and needs an expert’s help immediately. You see a number which you call in order to remediate the problem. In most cases, the contact is a threat actor and was also responsible for the current condition of your system. Thus, the threat actor will scam your money successfully.
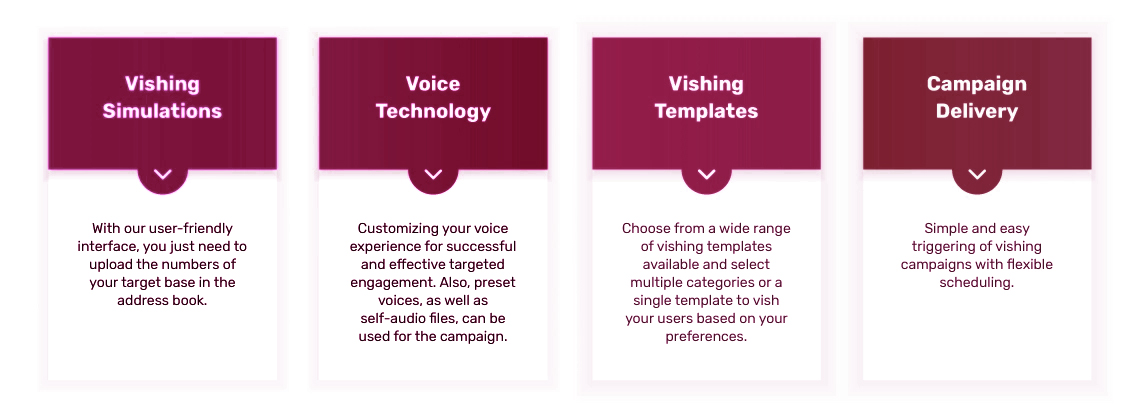
Aware provides phishing simulations that imitate real-life attack scenarios that teach your employees to spot phishing scams and prevent the hefty cost of data breaches.