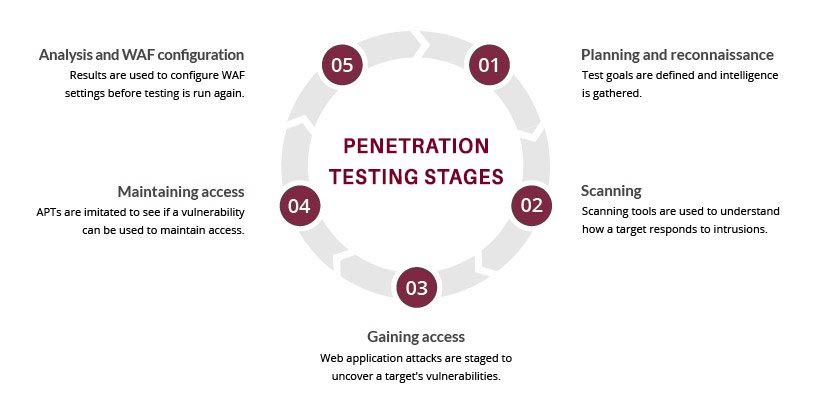
Step One – Discovery:
1.Retrieve the banners of network services and identify types and versions of software installed on the target Browse sites in their entirety in order to identify the different pages that are accessible directly (using the links on the main page) and indirectly
2.Using tools for enumeration of resources to identify the service provider or hidden but accessible resources that may contain relevant information in the context of the audit. Identify management and administration services
3.Use the Internet or internal SEO services such as search engines to identify all relevant information in the context of the audit (old resources or site structures, discussions on setting up the service in technical forums, configuration information, or user accounts stored on collaborative services such as shared calendars
Step Two - Vulnerability identification:
The objective of this activity is to identify security loopholes in different components of the network. With the profile of the target network, the security posture of the network segment (as a whole) is evaluated by passively and actively testing all the connection points of the network hosts on that network, and by identifying potential vulnerabilities exposed by these targets.
Broken Access Control: Access control enforces policy such that users cannot act outside of their intended permissions. Failures typically lead to unauthorized information disclosure, modification, or destruction of all data or performing a business function outside the user's limits.
Cryptographic Failures: Determine the protection needs of data in transit and at rest. For example, passwords, credit card numbers, health records, personal information, and business secrets require extra protection, mainly if that data falls under privacy laws, e.g., EU's General Data Protection Regulation (GDPR), or regulations, e.g., financial data protection such as PCI Data Security Standard (PCI DSS).
Injection: Automated testing of all parameters, headers, URL, cookies, JSON, SOAP, and XML data inputs to hostile data. Some of the more common injections are SQL, NoSQL, OS command, Object Relational Mapping (ORM), LDAP, and Expression Language (EL) or Object Graph Navigation Library (OGNL) injection.
Insecure Design: Insecure design is a broad category representing different weaknesses, expressed as “missing or ineffective control design.” Insecure design is not the source for all other Top 10 risk categories.
Security Misconfiguration: The application might be vulnerable if the application is Missing appropriate security hardening across any part of the application Unnecessary features are enabled or installed Default accounts and their passwords are still enabled, etc.
Vulnerable and Outdated Components: You are likely vulnerable if you do not know the versions of all components you use. If the software is vulnerable, unsupported, or out of date. This includes the OS, web/application server, database management system (DBMS), applications, APIs and all components, runtime environments, and libraries.
Identification and Authentication Failures: Confirmation of the user's identity, authentication, and session management is critical to protect against authentication-related attacks. There may be authentication weaknesses if the application permits automated attacks such as credential stuffing, where the attacker has a list of valid usernames and passwords.
Step Three - Exploitation and Analysis:
In this step, vulnerabilities/security observations from the previous phase are analyzed and/or exploited. The detected vulnerabilities are exploited and infiltration attempts to the internal systems are carried out after getting proper approval from the Client’s trusted agent.
Tasks The objective of this activity is to exploit the identified vulnerability. the vulnerabilities are found to be exploitable, this information is communicated to the Client’s trusted agent and an approval to exploit is obtained from the Client.
After cross-referencing and verifying vulnerabilities identified against databases of known vulnerabilities, these vulnerabilities are actively tested further to provide aggregation launch points. A series of sophisticated tests then follows, where the team leverages extensive experience and attack profiles, test scripts, and exploit programs to attempt to compromise the security of the target environment.
● Analyze the vulnerabilities in order to identify the exploitation and infiltration steps that can be performed.
● Communicate the exploitation activity with the trusted agent and obtain the confirmation before performing the actual exploitation steps on the target environment.
● Perform exploitation steps.
● Analyze the exploited vulnerabilities in order to identify the scope of infiltration.
● Record steps and results in Exploitation Details.
Step Four – Reporting:
The objective of this step is to create a detailed technical report and management executive summary detailing the activities performed and the security vulnerabilities and observations identified on the target operating system environment. The reports are prepared based on the format agreed upon by iSec SBA and the Client. The final report will mainly include the following:
- Vulnerability name and description
- Action performed on the target environment and its result.
- The root cause of the vulnerabilities identified.
- Severity Rating.
- Mitigation steps.
- Effort to fix the vulnerability.
Vulnerability identification:
The objective of this activity is to identify security loopholes in different components of the network. With the profile of the target network, the security posture of the network segment (as a whole) is evaluated by passively and actively testing all the connection points of the network hosts on that network, and by identifying potential vulnerabilities exposed by these targets.
-
Improper Platform Usage: The exposed service or API call is implemented using insecure coding techniques that produce an OWASP Top Ten vulnerability within the server.
-
Insecure Data Storage: Insecure data storage vulnerabilities occur when development teams assume that users or malware will not have access to a mobile device’s file system and subsequent sensitive information in data stores on the device.
-
Insecure Communication: Mobile applications frequently do not protect network traffic. They may use SSL/TLS during authentication but not elsewhere. This inconsistency leads to the risk of exposing data and session IDs to interception.
-
Insecure Authentication: Poor or missing authentication schemes allow an adversary to anonymously execute functionality within the mobile app or backend server used by the mobile app.
-
Insufficient Cryptography: In order to exploit this weakness, an adversary must successfully return encrypted code or sensitive data to its original unencrypted form due to weak encryption algorithms or flaws within the encryption process.
-
Insecure Authorization: To test for poor authorization schemes, testers can perform binary attacks against the mobile app and try to execute privileged functionality that should only be executable with a user of higher privilege while the mobile app is in ‘offline’ mode.
-
A network penetration test, often known as a pen test, tries to identify weaknesses in a network in the same way as vulnerability assessments do but a penetration test, unlike a vulnerability assessment, is a precise simulation of a real-world attack to detect flaws in a network that are harder to find
-
While automated testing improves efficiency and saves time, it is only useful in the early stages of a penetration test. At Isec, we believe that the only way to do a thorough and effective network penetration test is to use manual testing approaches and methodologies to dig even deeper into the network to uncover the hidden vulnerabilities that are hard to cover using automated testing and scanners.
-
Information gathering (reconnaissance), threat modeling, vulnerability analysis, exploitation, and reporting are all part of iSec's penetration testing methodology for assessing specific Internet-facing and internal systems and it is for us to guarantee to provide our customers a thorough, clear penetration testing report followed with the steps needed to fix all of your vulnerabilities.
-
Wireless network security is typically provided by wireless devices (typically a wireless router/switch) that by default encrypt and secure all wireless traffic. The hacker cannot see the content of the traffic/packet in transit even if the wireless network security is breached
-
Furthermore, here at iSec, we can provide thorough feedback about your wireless security and how to protect it, even more, to be always one step ahead of a hacker.
-
iSec's penetration testers simulate what would attackers do and try to break into your system during wireless penetration testing, Unlike other forms of penetration testing, they concentrate solely on exploiting wireless services that are accessible to everyone within a reasonable distance of your network.
Examples include:
- WiFi hotspots
- Wireless keyboards and mice are examples of wireless gadgets.
- Networks of cells
- Printers and scanners that are wireless
- Bluetooth enabled devices
- RFID and other RF technologies
iSec's penetration testers can evaluate your security and provide ideas to strengthen it by putting the security of your wireless to the test. Vulnerabilities can be addressed, new technology or architecture deployed, and new security rules implemented.


